The importance of secure boot in an OT network
The attack on the power grid in Ukraine in 2012 is an example of just how sophisticated an attack can become. Along with other less well-known attacks, this one involved injecting code into the operating system running on OT (Operational Technology) devices. The inserted code gave the crackers/attackers (actors) control over the OT network with the intention of sabotaging or influencing its operation.
As a result of Ukraine's attack, sections of the grid were shut down. Not only were breakers shut off and UPSs (Uninterruptible Power Supplies) instructed to shut down, but the entire communication system was disabled. The SCADA was rendered inoperable for several days. Other, less obvious, but no less damaging, attacks have taken place around the world where equipment has been intercepted in transit and modified software has been loaded on OT devices, allowing backdoors into the communications network. The intention being to eavesdrop on communications or allow access to assets on the target networks.
As part of this cyberattack, a hole in the bootup process is exploited where software integrity is not verified and validated during low level bootup. The integrity check ensures that the code being run is from the actual manufacturer and has not been modified or cracked. For devices to be protected from this type of attack, they must be able to verify the integrity of software through a method known as Secure Boot.
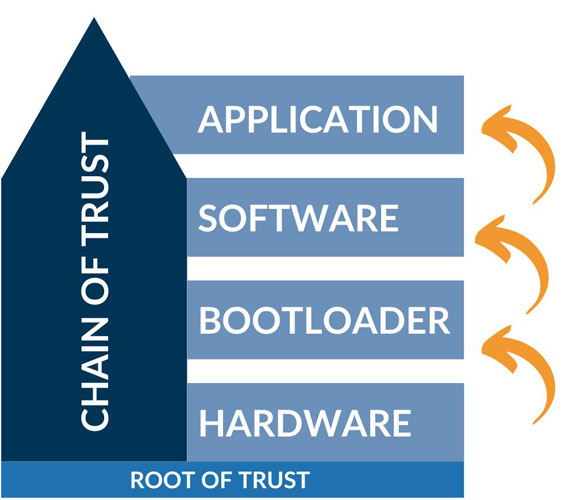
Secure Boot is not just a calculation of a checksum and a comparison against a known value, it also involves cryptography. At every step of the booting process, an unbroken chain of trust is established using digital signatures and certificates derived from a CA (Certificate Authority). A properly implemented Secure Boot process ensures an unbroken chain of trust through the entire supply chain, from the CA (Certificate Authority), to the R&D software department of the equipment manufacturer, to the hardware manufacturing process, and finally to the end devices. Only with a complete and unbroken chain of trust can an end user be assured that any attempt to run modified code will be detected. This will prevent it from getting to the point where the device is compromised.
Describing the Secure Boot process in depth is outside of this brief explanation. At a high level, Secure Boot begins with a Private and Public key being leased from a CA (Certificate Authority). These keys are used to digitally sign all software components within the chain of trust. During manufacturing of the device, a hash of the Public Key is permanently burned into a specialised one-time programmable memory fuse embedded on the PCB (Printed Circuit Board). A dedicated one-time programmable memory fuse should not be confused with a TPM (Trusted Platform Module). The TPM chip is used to securely store private keys installed by the user for use with TLS (Transport Layer Security) or VPN (Virtual Private Network). The TPM’s content can be erased, and new certificates can be loaded at any time making it an insufficient solution for Secure Boot. It is important to note, the information burned to the one-time programmable memory fuse is considered as the Root of Trust, and the fact that it is non-erasable nor modifiable makes it a fundamental component of the Secure Boot solution.
During the bootup of the device, the information burned on the hardware, in the one-time programmable memory fuse, is read and used to verify the Bootloader’s integrity via checksum and digital signature validations. At this stage of the booting process, the hardware verifies the low-level software known as the bootloader. After the bootloader has successfully booted up the hardware, it repeats the digital signature validation process to verify the digital signature of the operating system and software components on the device. The booting process will be terminated if at any point the process detects that the integrity of the loaded software component has been compromised. Then, the device will reboot while attempting to load the last working software. The Merlin family of cellular routers always have two images stored on the device’s flash memory. Should the primary image fail, the secondary image will be used to boot up the device. Hardware Secure Boot provides the ultimate solution to prevent attacks targeting the integrity of software components and ensures the authenticity of the running system.

Featured product
The robust and compact Merlin 4400 cellular router is the ideal fit for utility and industrial applications. Featuring zero-touch large-scale deployment and comprehensive cybersecurity capabilities, such as secure boot and TPM (Trusted Platform Module).
Learn moreMore applications to explore

Implementing IEC 62351
IEC 62351 is an industrial standard for improving security in industrial systems, specifically in power systems.

Secure boot in OT networks
Secure boot is the ideal solution for protecting software components from attacks and ensuring the authenticity of running systems.

Achieving security end to end
With many more distributed edge devices, securing the devices, network, cloud, and connected systems has never been more critical.
Explore all remote access solutions
For decades we have offered products and solutions for remote access networking applications. Our extensive product range and deep understanding of applications ensure that we can offer the best solution for your needs.

Remote access for utility applications
Cellular connectivity enables the ability to monitor sites holistically.

Remote access for industrial applications
Gain an overview of sites that were either once manned or relatively invisible.

Cyber-securing remote networks
Keeping your remote industrial networks and systems secure has never been more critical.

Zero touch networks
Cost effectively deploy and carry out maintenance of thousands of routers.

Protocol conversion
Protocol conversion enables one common stream of data to be transmitted or received to the top-end SCADA.

Legacy modem replacement
Migrate legacy serial devices from dial-up or leased line modem communications to serial over IP broadband.
Carl de Bruin
International sales

Behöver du teknisk hjälp? Klicka här för att kontakta vår support
