Cybersecurity in Industrial Networks: Strategies Beyond Passwords
When most people think of cybersecurity, the first thing that comes to mind is changing default passwords. While that’s a good start, it barely scratches the surface. In today’s digital landscape, especially within Operational Technology (OT) environments like utilities, transportation, and energy, cybersecurity demands proactive behavior, policy-based management, and constant vigilance.
Here is a break down some of the most common types of cyberattacks targeting OT Systems and how to spot them before they cause serious disruption.
Malware: Hidden & Harmful
Malware, short for "malicious software," is designed to infiltrate, exploit, and damage systems. It often arrives via email attachments, giving attackers access to sensitive data or even locking systems for ransom.
Common types of malware include:
Spyware: Secretly monitors user activity.
Ransomware: Encrypts data and demands payment for release.
Tip: Always check file attachments to see if they are suspicious. File types such as .bat can run scripts on your machine, where others could be hidden in generic file types such as PDFs. If you are unsure - don’t download it and contact your local IT department.
Phishing: Hook, Line, and Deception
Phishing is a classic scam where attackers impersonate trusted entities to trick users into revealing information. These emails often look legitimate, complete with logos and formatting, but contain hidden malicious links.
Red flags to watch for:
• Urgent requests for data
• Unusual sender addresses
• Generic greetings
Remember: Do not provide information to anyone you don’t trust, esepcially if it is sensitive such as usernames and passwords.
Spear Phishing: Precision Targeting
Unlike general phishing, spear phishing is tailored to specific individuals or organisations. Attackers research their targets and craft personal, convincing emails that appear to come from colleagues or internal departments.
Example: An email from info@westermo.com might actually be info@westerno.com.
At a glance, the “r” and “n” can look like an “m.” - This is esepcially common when people are very busy and may not noticed a small difference. Since these are usually targeted they aim to catch people off guard.
Additionally, they could also come from someone pretending to be someone else. This could well be from an recognised name or email, possibly someone senior in the organisation. Usually, the email contains hints to an attack such as pressure to send documents (financial, sensitive), along with time limits (i.e., as soon as possible) to encourage you to fall for the deception.
Tip: Always double-check sender addresses if you are not sure and report it to your local security department.
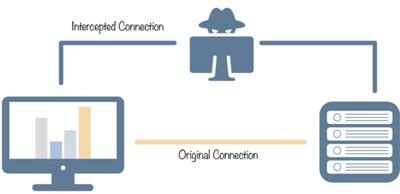
Man-in-the-Middle (MiTM): Eavesdropping in Disguise
MiTM attacks occur when a third party intercepts communication between two systems. Imagine Alice and Bob exchanging data over a network, unbeknownst to them, Eve is secretly listening in. The threat here is that information that is intercepted could be viewed or modified. Secure communication via VPNs or using HTTPs can help prevent eavesdroppers from viewing data.
Real-world case: In 2017, the KRACK vulnerability in Wi-Fi encryption allowed attackers to bypass HTTPS and view sensitive data in plain text via HTTP
Defense: Use encryption and keep firmware updated to patch known vulnerabilities. Try and avoid using HTTP only websites that require a username and password.
Distributed Denial of Service (DDoS): Overload and Outage
DDoS attacks flood networks with traffic from multiple sources, rendering systems unusable. These attacks can last hours, days, or even weeks, causing massive disruption.
Prevention tips:
• Deploy firewalls
• Avoid exposing devices directly to the internet
• Monitor traffic for unusual activity
• Turn off ununsed management services
Insight: If attackers can’t find your system, they can’t target it.
Insider Threats: Understanding the human element
Sometimes, the threat comes from inside. Disgruntled employees or careless insiders can cause significant damage, intentionally or not.
Mitigation strategies:
• Limit access to only those who need it
• Implement shared responsibilities
• Foster a culture of trust and collaboration
• Provide systems for people to report incidents
Rememeber: Overly restrictive policies can backfire. It is important to trust people, but be cautious of attack vectors.
Cybersecurity Means Teamwork
Securing industrial networks isn’t just about technology, it’s about people. Regular training, clear policies, and open communication between employees and employers are essential. Cyber threats are evolving, and so must our defenses. Cybersecurity isn’t a checklist. It takes time, team effort and trust to ensure OT networks remain safe and secure.
See also

Differences between OT and IT security
Learn how industrial networks face unique risks, why resilience is critical for OT environments, and discover practical steps to strengthen cybersecurity in both domains.

Six easy steps to secure your networking device
To reduce the risk of cyber attacks and increase network security, we have developed six simple steps that you can follow.
Carl de Bruin
International sales

For support inquiries, click here to contact Technical Support